Malware Detection
Malware scanning
In artifact management, malware scanning is the process of inspecting software packages, container images, and dependencies for malicious code before they are stored in a repository or used in a build. This is a critical step in securing the software supply chain.
Note
📘 Malware scanning via ClamAV is included in all Cloudsmith plans.
How it works
Cloudsmith uses a signature-based detection engine that compares your artifacts against a library of known malware “fingerprints”.
Each piece of malware has unique characteristics, or "signatures", that can be used to identify it. A signature might be:
- A specific byte sequence from the malware's code
- A cryptographic hash of a malicious file
- Another distinct pattern unique to the malware
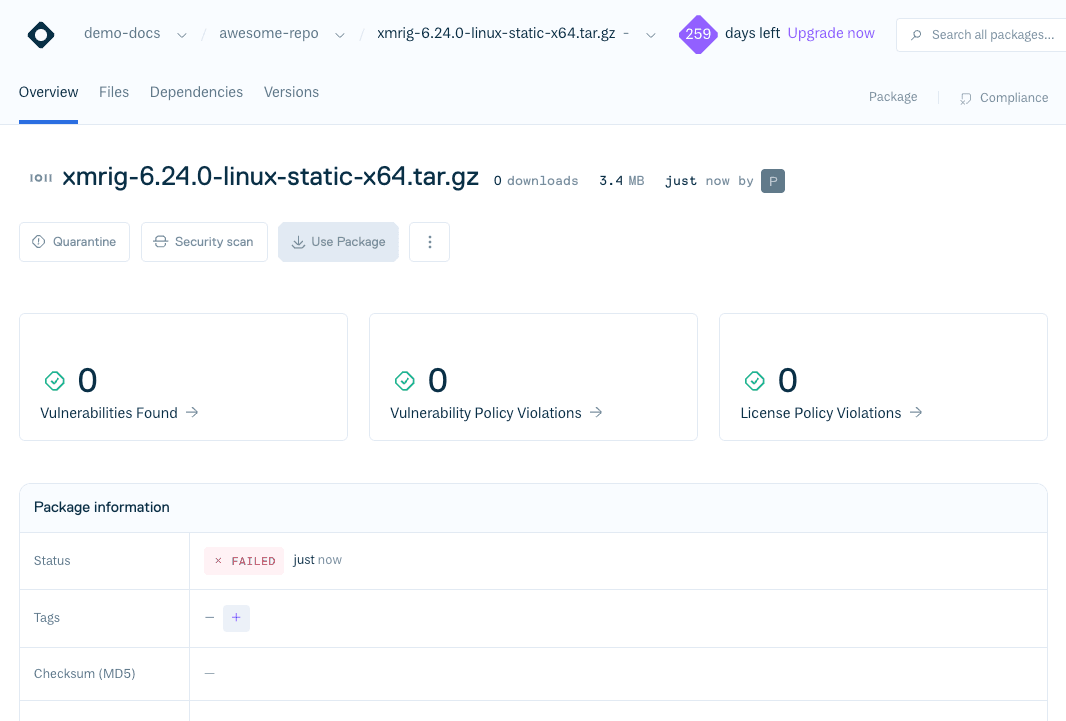
Before any artifact is synchronized, its files are scanned. If the scanner detects a match in the malware signature database:
- The artifact is flagged as malicious
- Synchronization fails, and the package status is set to
FAILED - The package is blocked from being downloaded, copied, moved, or otherwise used
For example, trying to upload a malicious file from a terminal will result in the following output:
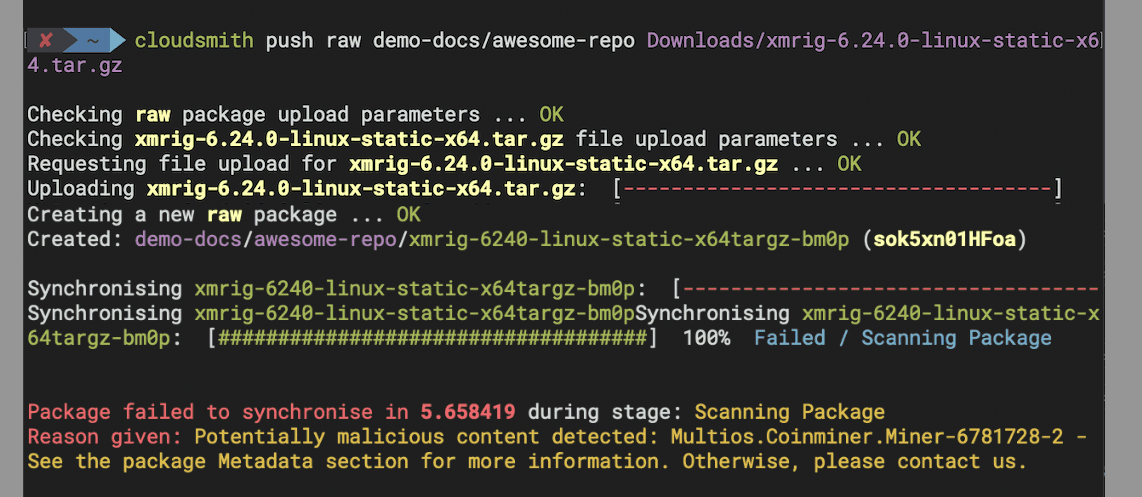
Even if you retry synchronization, it will fail until the issue is resolved, effectively eliminating the risk.
Sample malware: eicar
To test the scanner without using real malware, you can use the harmless sample malware file. This file contains a known signature in the malware database, and you can use it to test any malware scanner.
First, upload the file using the Cloudsmith CLI with:
cloudsmith push raw WORKSPACE/REPOSITORY ./eicar.com.txtNow, we can get more information and retrieve package metadata with the API. First, update the envvars with your own data, and then get the package identifier (slug_perm):
API_TOKEN=
WORKSPACE=
REPO=
curl -s -X GET \
'https://api.cloudsmith.io/v1/packages/WORKSPACE/REPO/' \
-H 'accept: application/json' \
-H 'X-Api-Key: API_TOKEN' \
| jq '.[] | "\(.name) \(.slug_perm)"'
| grep eicarUsing the package id (in this case IfwsHhsYbTaB ), we can retrieve the status reason and more information from its metadata fields:
curl -s -X 'GET' \
'https://api.cloudsmith.io/v1/packages/WORKSPACE/REPOSITORY/IfwsHhsYbTaB/' \
-H 'accept: application/json' \
-H 'X-Api-Key: API_TOKEN' \
| jq '{ status: .status_reason, malware: .extended_metadata.Malware }'{
"status": "FAILED",
"malware": "Potentially malicious content detected: Win.Test.EICAR_HDB-1 - See the package Metadata section for more information. Otherwise, please contact us."
}Here, the initial scan detected malicious content and automatically blocked synchronization.
Supported Formats
| Package Format | Supported Archive Types |
|---|---|
| Python | zip (.whl), tar.gz |
| Java/Maven | zip (.jar) |
| NuGet | zip (.nupkg) |
| npm | tar.gz (.tgz) |
| Helm | tar.gz (.tgz) |
| Conan | zip, tar.gz |
| Raw files | Scanned based on file type |
Conclusions
Malware scanning is a foundational security layer in Cloudsmith. Every artifact is scanned before it's made available—helping protect your infrastructure and end users from compromised code.
For additional protections against other subtypes of malware like malicious packages, see Malicious Packages.